Staying ahead of cyber threats in today’s dynamic digital landscape poses significant challenges for organizations. The sheer volume of data to process and the need for swift, effective incident response make managing security a complex task. Microsoft Security Copilot is here to help with this issue.
Microsoft Security Copilot is a groundbreaking AI-powered cybersecurity solution. Designed to provide tailored insights, Copilot empowers security teams to defend their networks efficiently. It seamlessly integrates with other Microsoft security products and utilizes natural language to generate personalized guidance and insights.
In this article, we’ll delve into what this new tool offers, its benefits, and whether it’s the right fit to bolster your digital defenses.
What Is Microsoft Security Copilot?
At its core, Microsoft Security Copilot is an innovative cybersecurity tool leveraging AI and machine learning for threat detection and response. It aims to enhance the efficiency and effectiveness of cybersecurity operations by assisting teams in responding to threats, processing signals, and assessing risk exposure at machine speed.
Microsoft Security Copilot helps security teams:
- Respond to cyber threats
- Process signals
- Assess risk exposure at machine speed
One of the key advantages is its integration with other Microsoft security products, allowing for a comprehensive security ecosystem. Additionally, its natural language integration enables users to seek tailored guidance and insights simply by asking questions.
Security Copilot can help with end-to-end scenarios such as:
- Incident response
- Threat hunting
- Intelligence gathering
- Posture management
- Executive summaries on security investigations
How Does Microsoft Security Copilot Work?
Microsoft Security Copilot can be accessed through both standalone and embedded experiences within other Microsoft security products. It seamlessly integrates with various tools, including Microsoft Sentinel, Microsoft Defender XDR, and Microsoft Intune, among others.
Users can leverage natural language prompts to request information or guidance on diverse security topics, streamlining the process of threat analysis and response.
You could ask:
- How can i secure Azure workloads to meet best practices?
- What is the impact of CVE-2024-23905 on my organization?
- Generate a report on the latest attack campaign.
- How do I remediate an incident involving TrickBot malware?
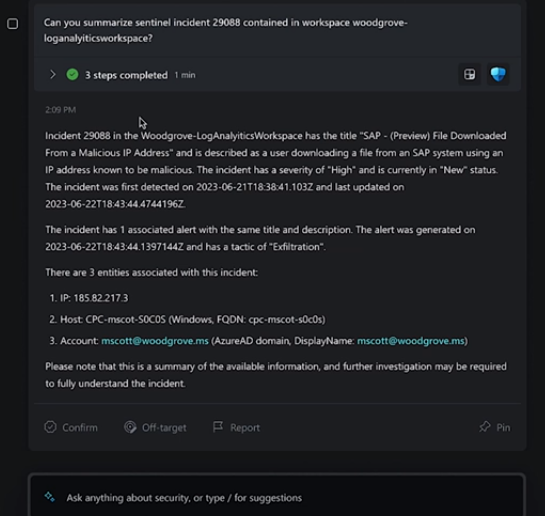
Should You Use Microsoft Security Copilot?
The Pros:
- Advanced Threat Detection
Microsoft Security Copilot utilises advanced algorithms to detect and analyse threats, even those that may evade traditional security measures, thereby enhancing organisational security posture.
- Operational Efficiency
By automating threat analysis, Copilot enables security teams to focus on strategic decision-making, streamlining workflows and facilitating quicker responses to potential threats.
- Integration with Microsoft Products
Seamless integration with multiple Microsoft products creates a comprehensive cybersecurity ecosystem, enhancing threat visibility and response capabilities.
- Continuous Learning
The AI and machine learning components of Copilot continuously evolve and adapt to new data, improving their ability to identify and mitigate emerging threats over time. Reduced False Positives: Advanced algorithms contribute to a more accurate threat detection process, minimising false positives and enabling a more focused response to genuine threats.
The Considerations:
- Integration Challenges
While Copilot integrates seamlessly with Microsoft and other security products, organisations with diverse cybersecurity toolsets may face integration challenges.
- Resource Requirements
Deployment of advanced AI and machine learning technologies may require additional resources, necessitating compatibility checks with existing infrastructure.
- Training and Familiarization
Leveraging Copilot effectively requires training and familiarity with its functionalities, ensuring the security team can maximise its potential.
The Bottom Line
Microsoft Security Copilot offers a significant advancement in AI-driven cybersecurity, boasting real-time threat detection, operational efficiency, and extensive integration capabilities. However, the decision to adopt Copilot should be guided by your organisation’s specific needs and considerations, including existing cybersecurity infrastructure, resource availability, and commitment to ongoing training.
Get Expert Microsoft Product Support Here!
If you’re seeking expert support in leveraging Microsoft’s suite of tools, including Security Copilot, our team of experienced Microsoft service providers is here to help you maximise their potential and strengthen your online security posture.
Contact us today to schedule a consultation.












